GitHub Management Policy
DSACMS Organization
Table of Contents
GitHub Organization Access
Setting up a Help Desk
Help Desk Team & Repository Requests
- Request a new team to be created for a Project
- Request access to a team as a member
- Request a new repo to be created
Repository-Level Access Requests
- Request a new team to be added to a repo
- Request an outside collaborator to be added to a repo
- Request a third-party integration to be added to the repo
Repository Metadata
GitHub Organization Management
FAQs
GitHub Organization Access
Setting up a Help Desk
A help desk serves as the center for GitHub Organization Access and Management.
Help Desk Team
The help desk team consists of organization members with the following roles and permissions below:
- All-repository maintain: Grants maintenance access to all repositories in the organization
- All-repository admin: Grants admin access to all repositories in the organization
- CI/CD admin: Grants admin access to manage Actions policies, runners, runner groups, network configurations, secrets, variables, and usage metrics for an organization
- Security manager: Grants the ability to manage security policies, security alerts, and security configurations for an organization and all its repositories
See list of organization roles here: https://docs.github.com/en/organizations/managing-peoples-access-to-your-organization-with-roles/using-organization-roles
Help Desk Repository: A centralized approach for managing team and repository creation requests
Requests for team/repository creation should be filed through a central repository managed by the Help Desk team. Project teams file an issue for the request under the repository. The help desk team is responsible for handling the request, working with the project team to ensure the task is completed and fulfills the needs of project teams.
Project Repository: A distributed approach for repository management
Requests for repository management should be filed through the project repository. Project teams file an issue under their repository, tagging the help desk team as the assignee. The help desk team is notified and will work with the project team to ensure repository and fulfill the needs of the project team.
Help Desk Team and Repository Requests
Requests to create and grant access to teams & repositories must be filed under the OSPO help desk repository for organization owners and help desk individuals to grant and manage accordingly.
Request a new team to be created for a Project
Step 1: Creating a Team with Project Maintainers - Maintainers Team
Project maintainers will be placed in their own separate team and serve as the main point of contact for coordinating team & repository management with the OSPO.
Information required:
- Project name
- Team name: projectName_maintainers
- List of GitHub usernames to be added
- Team visibility: visible or secret
Step 2: Creating a Parent Team with All Project Members - Committers Team
All project members will be under the member role where they have no administrative permissions on the team. Team visibility and notifications are enabled unless specified otherwise.
Information required:
- Team name: projectName_committers
- List of GitHub usernames to be added
- Team visibility: visible or secret
(Optional) Step 3: Creating Child Teams
Child teams can be granted additional and more granular access to certain repositories. Examples of child teams can include code reviewers, developers under a repo domain, and project leads.
Information required:
-
Team name: projectName_teamType
- Examples of team types: frontend team, backend team, reviewers
-
Team name: projectName_teamType
- Examples of team types: frontend team, backend team, reviewers
-
List of GitHub usernames to be added
Request access to a team as a member
The member will be under the member role where they have no administrative permissions on the team.
Information required:
- GitHub username
- Team name
Request a new repo to be created
If you are looking to migrate an existing repository hosted in a different organization into a new repository under DSACMS, the new repository will be created as private by default. In order for your repository to be released as public, please follow our outbound review checklist for your project’s maturity tier.
If you are looking to create a completely new repository, your repository can be created as private or public. Based on the maturity model tier selected, a collection of markdown templates will be included as part of our repository hygiene standards. GitHub security features such as Dependabot and secret scanning will be enabled.
For more information on repository creation using templates, visit:
Information required:
-
Repository Name
-
Repository Description
-
Project’s Maturity Model Tier
-
Repository Topics
-
Project teams to add to repository, such as:
- Maintainer team
- Committer team
- Any other teams/child teams
-
Project teams to add to repository, such as:
- Maintainer team
- Committer team
- Any other teams/child teams
-
Repository Visibility: private or public
- Include an assessment of benefits and risks of selecting this visibility
Repository-Level Access Requests
The Open Source Program Office is experimenting with a distributed-style approach of managing access requests. Requests to grant access to individuals and third-party integrations are filed under the repository for repository admins and organization owners to grant and manage accordingly.
Request a new team to be added to a repo
Maintainer teams have MAINTAIN access while committer teams have WRITE access. If you or other members want to be promoted to MAINTAIN access, please indicate this in the form. ADMIN access is only available to DSACMS organization owners for now. MAINTAINERS.md will be updated accordingly. Maintainer teams have MAINTAIN access while committer teams have WRITE access. If you or other members want to be promoted to MAINTAIN access, please indicate this in the form. ADMIN access is only available to DSACMS organization owners for now. MAINTAINERS.md will be updated accordingly.
Information required:
- Team name
- Team type: parent or child
- Repository name to be given access to
- Reason for access
Request an outside collaborator to be added to a repo
For individuals that are not members of the DSACMS GitHub organization, these outside collaborators can request access to a repository. Fill out this issue to file the request or make a pull request to the MAINTAINERS.md file, then a repository admin will grant access.
Information required:
- Name of individual
- GitHub username
- Repository to be added
- Role of the Outside Collaborator as listed in
MAINTAINERS.md- Maintainers, Approvers, Reviewers
- Any additional information
Request a third-party integration to be added to the repo
The DSACMS org uses the following third-party GitHub apps: SonarCloud. If your team would like to install and use an integration in your repository, please file a request by sending a slack message at #cms-ospo. We are open to adding more integrations to this list based on team needs.
Information required:
- Third-party Integration / GitHub App to be added
- Reason for usage
- Project’s Maturity Model Tier
- Keys that will need to be created
Repository Metadata
Every repository in DSACMS is required to have a code.json file containing project metadata. For details on metadata requirements, creation, and maintenance, refer to gov-codejson.
GitHub Organization Management
Monthly audit of membership
Members
Review the list of current organization members and their attributes:
- Is 2FA enabled?
- What is their role? (owner vs member)
- What team do they belong to? What are their member permissions?
Outside/Pending Collaborators
Review the list of outside collaborators and their attributes:
- Is 2FA enabled?
- What repositories do they have access to?
Invitations
Review the list of sent invitations and failed invitations:
- Assess whether to resend or delete failed invitations
Review activity log
The audit log for organization activity must be reviewed on a monthly basis. Export the log as a CSV and attach it to the name_of_ticket_here in internal CMS GitHub. Any org members can do this. https://github.com/organizations/DSACMS/settings/audit-log The audit log for organization activity must be reviewed on a monthly basis. Export the log as a CSV and attach it to the name_of_ticket_here in internal CMS GitHub. Any org members can do this. https://github.com/organizations/DSACMS/settings/audit-log
- Organization Membership
- Team Management
- Repository Management
- Billing Updates
- Copilot Activity
- Hook Activity
- Personal Access Token Activity
Security
Organization-wide Settings
Authentication Security
Two-factor authentication is required for everyone under the DSACMS organization.
Code Security
Review Code Security Configurations
https://github.com/organizations/DSACMS/settings/security_products
-
All repositories use the GitHub-recommended code security configuration:
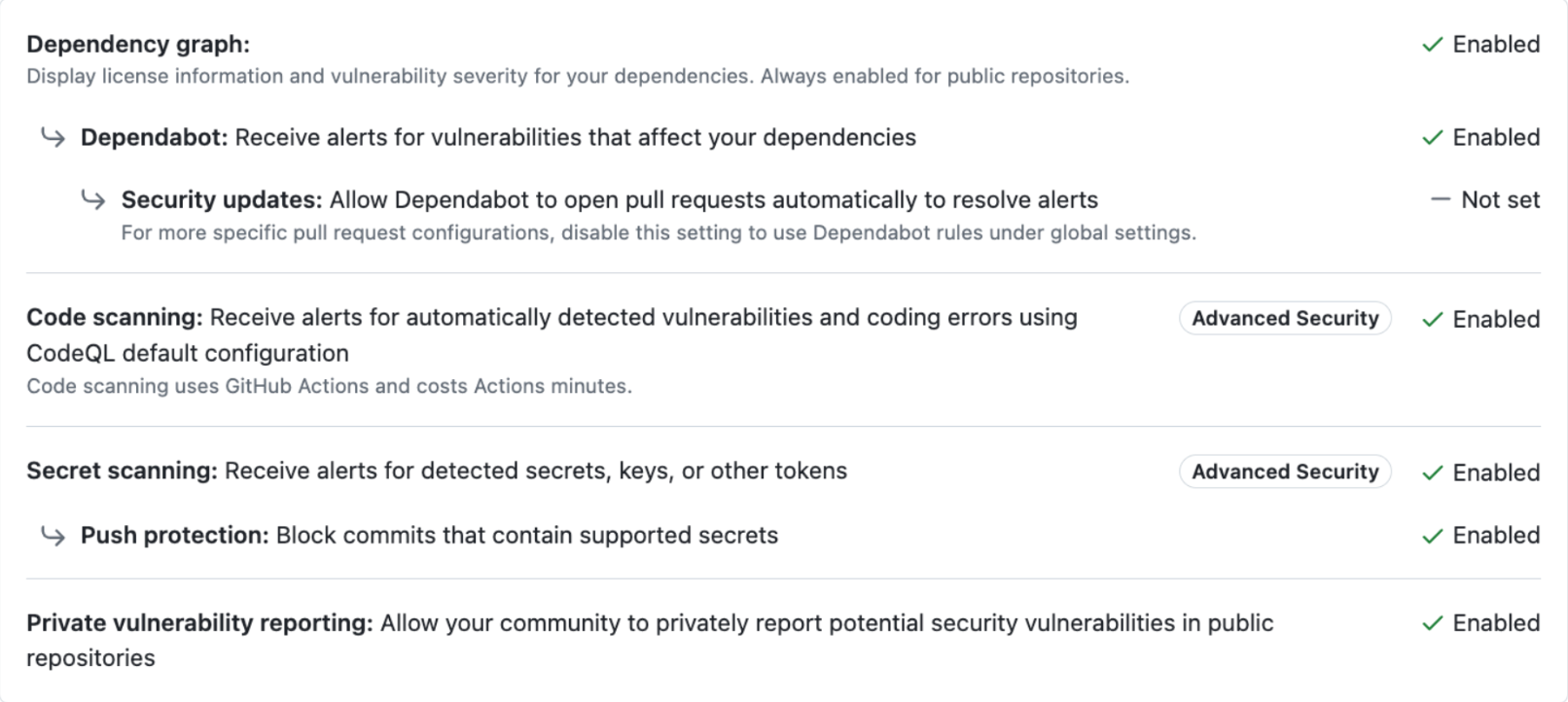
-
Currently, all public repositories under DSACMS use GitHub Advanced Security features (i.e. Code Scanning, Secret Scanning). Private repositories will only have free features enabled. features (i.e. Code Scanning, Secret Scanning). Private repositories will only have free features enabled.
Review Global Settings
https://github.com/organizations/DSACMS/settings/security_analysis
- Dependabot is enabled by default with a rule to dismiss low-impact alerts for development-scoped dependencies.
- Code scanning features will be enabled on a case-by-case basis.
Check Tokens & Keys
Personal Access Tokens
Review Tokens Settings
The active tokens must be reviewed on a monthly basis. Export the log as a CSV and attach it to the name_of_ticket_here in internal GitHub.
https://github.com/organizations/DSACMS/settings/personal-access-tokens/active
- Who is the owner?
- Does the token have organization and repository permissions and/or access?
- When was the token last used?
Requesting for Personal Access Tokens
Personal Access Tokens will be granted for repo permissions with read and/or write access. Organization permissions will require explicit permission.
Private Keys for GitHub Apps
Please review keys used for third-party apps and GitHub apps: https://github.com/organizations/DSACMS/settings/installations
Please review keys used for third-party apps and GitHub apps: https://github.com/organizations/DSACMS/settings/installations
Check Secrets
Actions Secrets & Variables
https://github.com/organizations/DSACMS/settings/secrets/actions
- Secrets and variables allow you to manage reusable configuration data. Secrets
are encrypted and are used for sensitive data.
https://docs.github.com/en/actions/security-guides/using-secrets-in-github-actions - Anyone with collaborator access to the repositories with access to a secret or variable can use it for Actions.
- Cannot be used in private repositories in our current plan.
Codespaces Secrets
https://github.com/organizations/DSACMS/settings/secrets/codespaces
- Development environment secrets are environment variables that are encrypted. They are available to any codespace user with collaborator access to the repositories with access to that secret.
- Cannot be used in private repositories in our current plan.
Dependabot Secrets
https://github.com/organizations/DSACMS/settings/secrets/dependabot
- Anyone with collaborator access to the repositories with access to each secret can use it for Dependabot.
Monitor usage under GitHub plan
The DSACMS GitHub Organization is currently under the GitHub free plan.
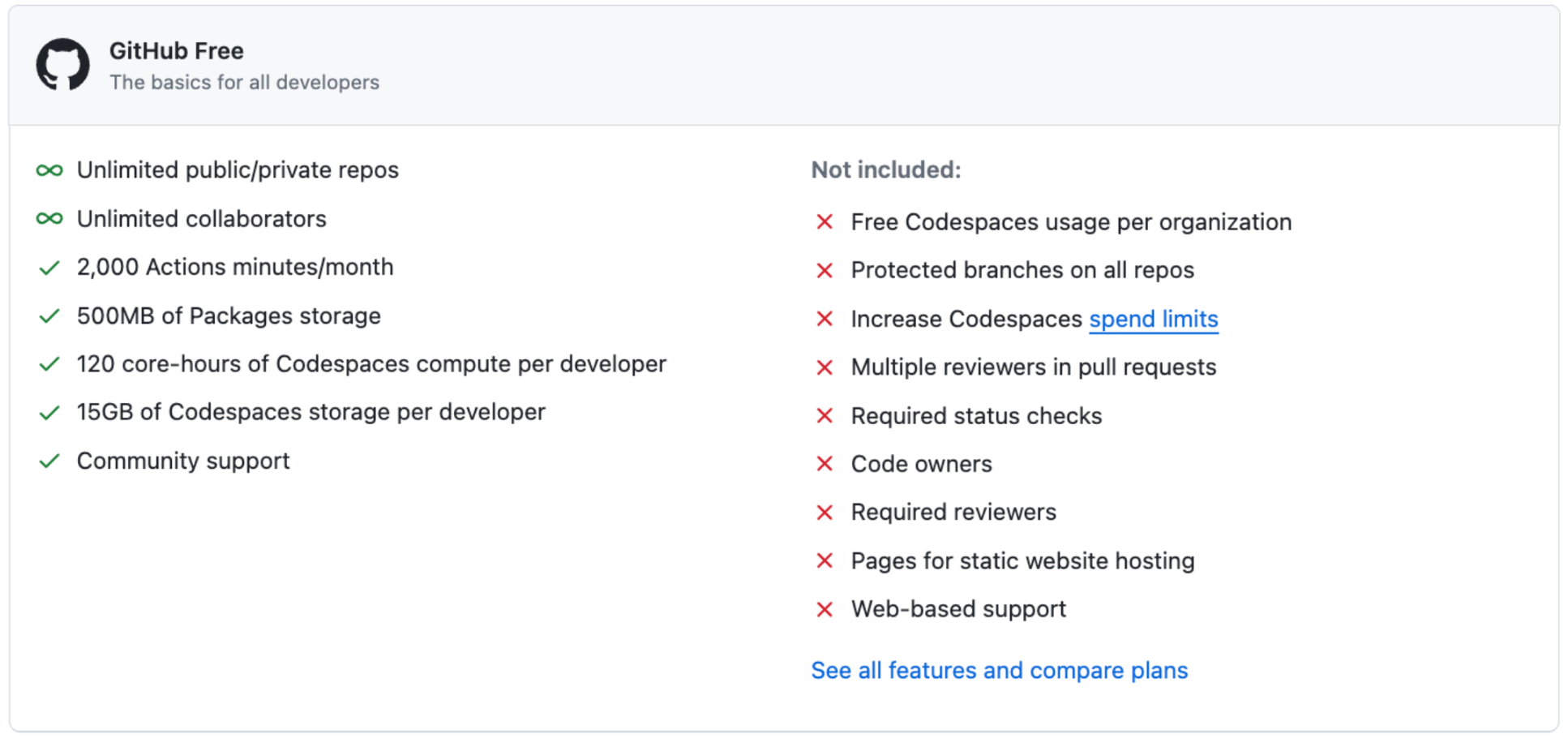
The usage of the features below must be reviewed on a monthly basis. Export this information into a report using the “Get Usage Report” button and attach it to the name_of_ticket_here in internal GitHub.
| Feature | Limit |
|---|---|
| GitHub Actions | 2,000 minutes |
| Packages | 1 GB |
| Storage for Actions and Packages | 0.5 GB |
| Codespaces: Usage hours | 120 core hours |
| Codespaces: Storage | 15 GB |
| Git LFS Data: Storage | 1 GB |
| Git LFS Data: Bandwidth | 1 GB |
FAQs
Can I be admin for a repository?
For now, no. Admin is only reserved for OSPO staff but as we continue to use this organization and form our GitHub policy guidance, this may change in the future.
How do GitHub Teams work? What are the differences between parent teams and child teams?
- Teams can only be made up of members of your organization, outside collaborators are unable to be on a team.
- You should give parent teams repository access permissions that are safe for every member of the parent team and its child teams. As you move toward the bottom of the hierarchy, you can grant child teams additional, more granular access to more sensitive repositories.
Can we add outside collaborators as code reviewers?
Yes! MAINTAINERS.md in the repository’s root directory is the ‘source of truth’ for this list of users. This file can be updated indirectly by creating an issue as noted in the outside collaborator section, or directly by creating a Pull Request with Name and github username for the collaborator under the Reviewers section. Once this list is updated, a repository admin can grant appropriate levels of access upon request in #cms-ospo or by filing a ticket.
 OSPO Guide
OSPO Guide
